Module 2: Quay and OpenShift Pipelines
Module Overview
This module introduces the integration of Quay as a container registry with OpenShift Pipelines using Tekton. By the end of this module, participants will understand how to configure and secure Quay within a CI/CD pipeline.
Key Learning Objectives
-
Understand the role of Quay as a container registry in the CI/CD pipeline.
-
Configuing your repo with a Quay Pull secret for your Tekton Pipelines.
-
Pre-Configuring your enviornment to push images to Quay using Tekton Pipelines.
-
Explore best practices for securing container images in Quay and within a CI/CD workflow.
Introduction to Quay
Red Hat Quay is a robust container registry that stores, builds, and deploys container images. In the CI/CD pipeline, Quay serves as a central repository for container images, facilitating efficient storage, versioning, and distribution. It also offers features like image vulnerability scanning and mirroring, enhancing security and reliability in the development workflow.
Integrating Quay with OpenShift Pipelines
To automate the CI/CD process, integrate Quay with OpenShift Pipelines (based on Tekton). This integration allows pipelines to push newly built images to Quay and trigger subsequent tasks, such as deployments or notifications. For instance, configuring Tekton pipelines to push images to Quay can be achieved by creating a secret with Quay credentials and referencing it in the pipeline tasks.
Steps for Integration:
-
Understand the Role of Quay: Learn how Quay operates as a container registry in the CI/CD pipeline and its importance in image storage and distribution.
-
Configure a Quay Pull Secret: Set up your repository with a Quay Pull secret to ensure Tekton Pipelines can pull required images securely.
-
Prepare the Environment: Pre-configure your environment to push container images to Quay during pipeline execution.
-
Create and Reference Secrets: Store Quay credentials securely in a Kubernetes secret and reference them in your Tekton pipeline tasks for seamless integration.
Security Considerations
Securing container images in Quay involves implementing best practices such as enabling image vulnerability scanning, using signed images, and enforcing access controls. Integrating security tools like Sigstore and Tekton Chains can further enhance the security posture by providing image signing and verification capabilities.
Best Practices for Securing Container Images:
-
Enable Vulnerability Scanning: Use Quay’s built-in image scanning capabilities to identify and address vulnerabilities proactively.
-
Enforce Signed Images: Leverage signing mechanisms to verify image authenticity and integrity.
-
Access Control: Restrict access to sensitive repositories and enforce role-based access controls.
-
Integrate Advanced Security Tools: Utilize tools like Sigstore and Tekton Chains to enable automated image signing and verification within the CI/CD pipeline.
Hands-on Exercise: Configuring Quay Integration
Exercise Objectives
-
Configure Quay as a container registry for your application.
-
Set up necessary credentials and modify pipeline configurations to push images to Quay.
-
Implement security measures such as enabling image scanning and signing to ensure the integrity and security of your container images.
Login to OpenShift Cluster
Ensure you are logged in to your OpenShift cluster using the appropriate credentials.
-
Username: {additional_user}
oc login -u <username> -p <password> <cluster-url>Configure Gitea
Access the Gita URL
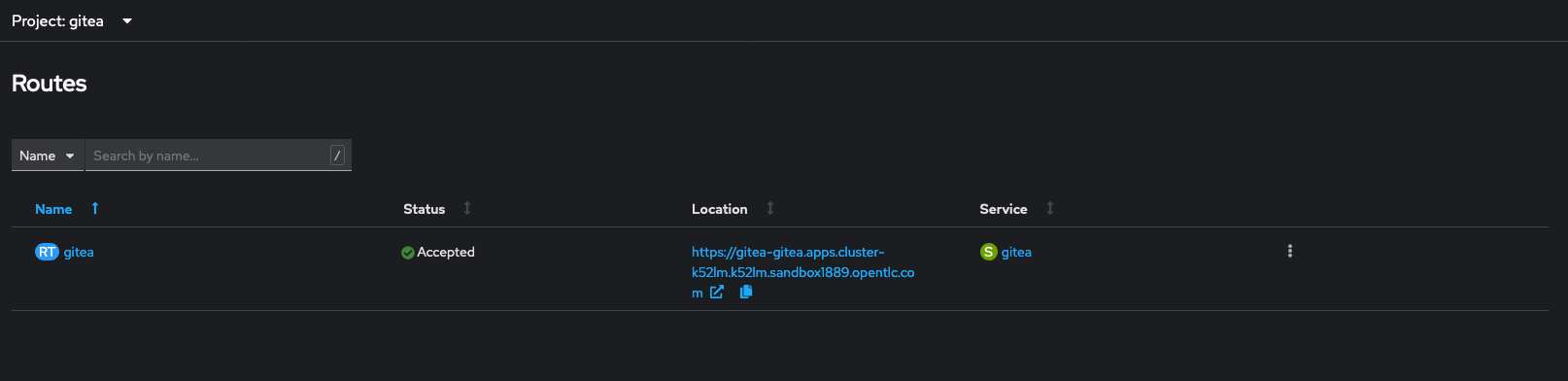
Using OpenShift CLI
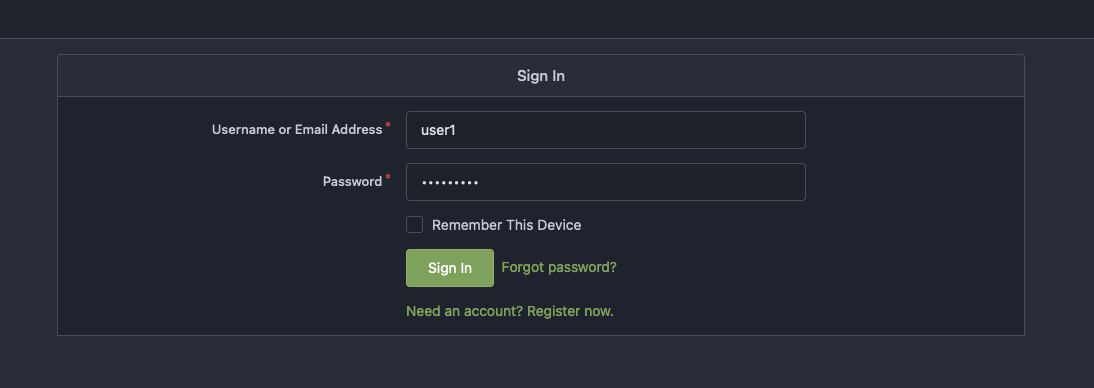
echo "USER ME: $(oc get route -n quay-registry | grep quay-registry | awk '{print $2}')"Login using your username and password
Configure Quay
Access the Quay repo URL
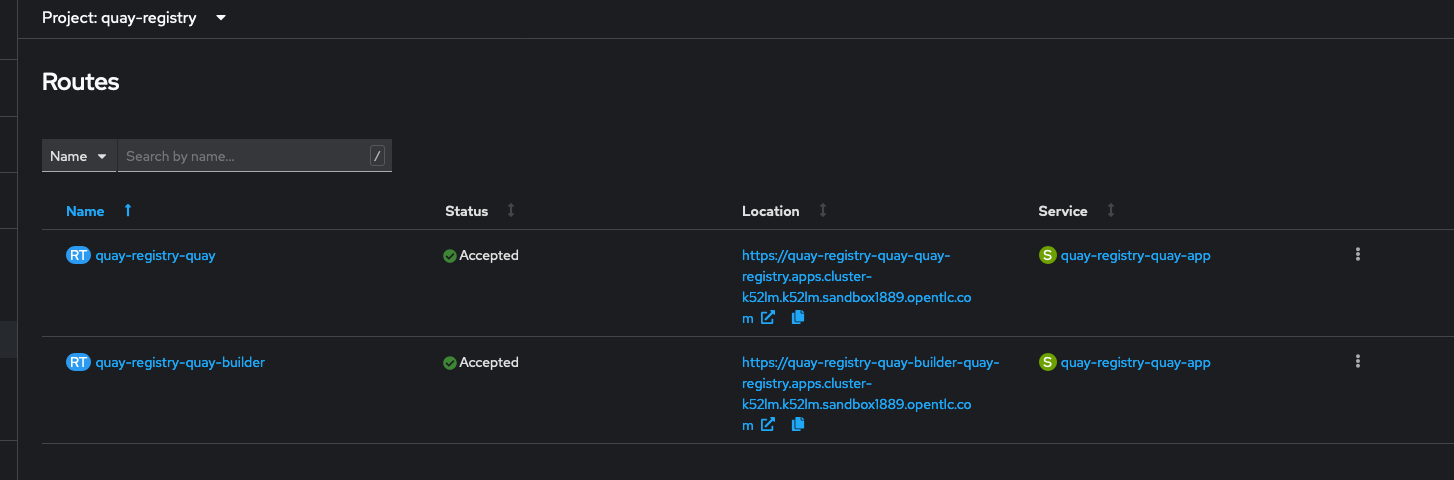
Create User account in Quay
-
Username: your-username
-
Email: your-username@example.com
-
Password: quay-playground
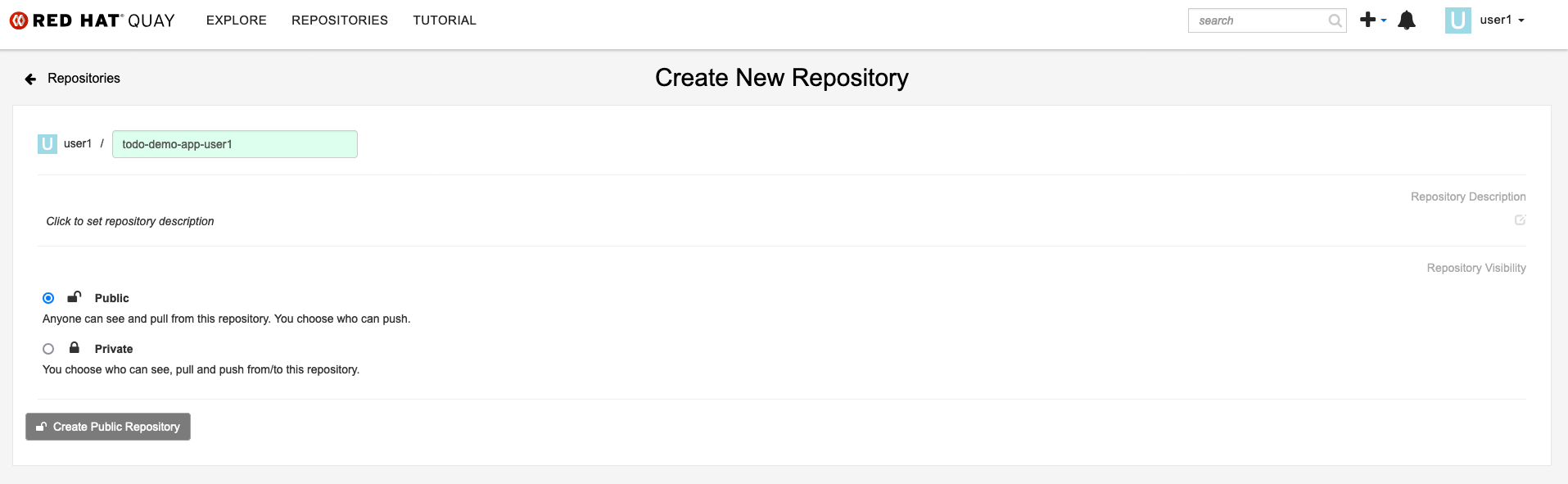
Create todo-app Repository
| REPONAME: todo-demo-app-yourusername |
Create Robot accout for Repo
| Click on Account Settings |
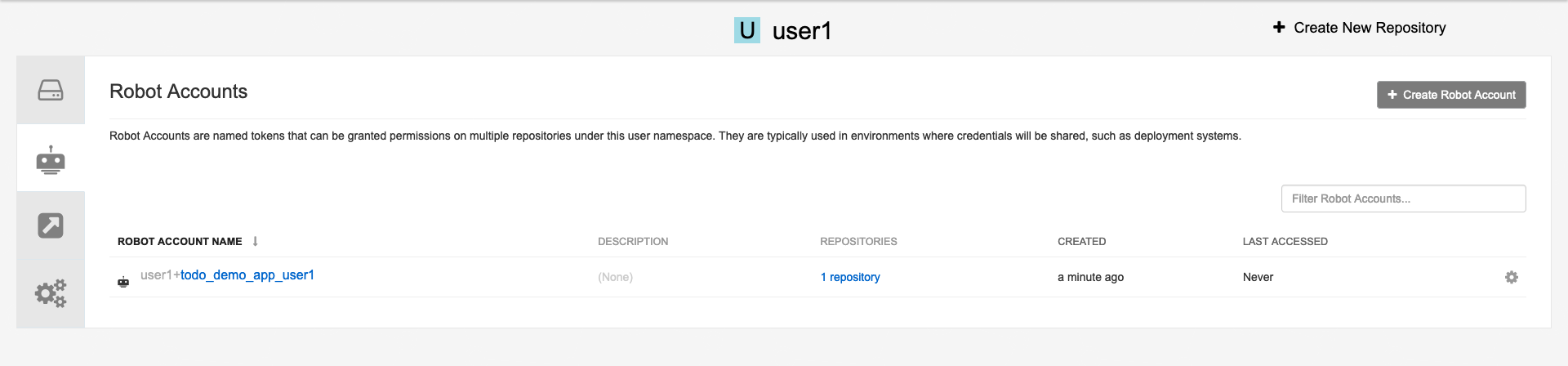
Click on Robot Accounts
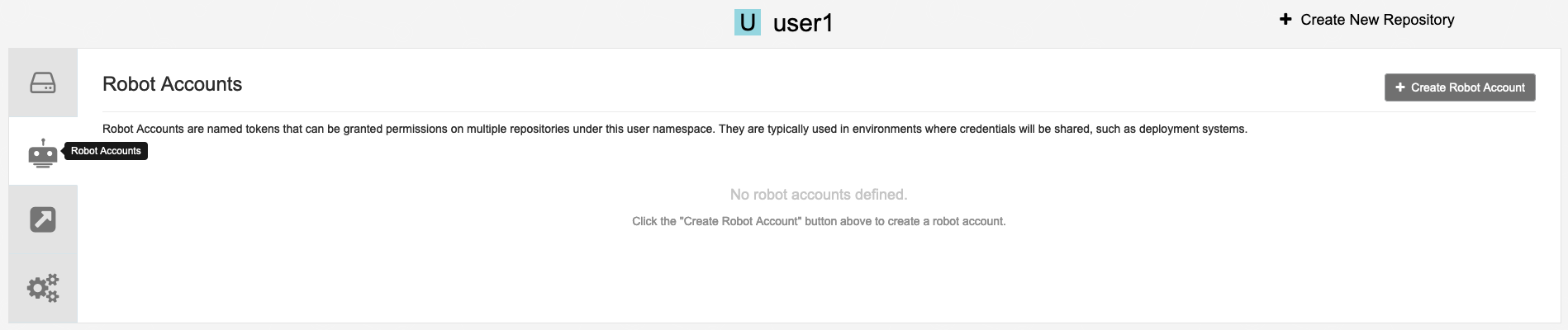
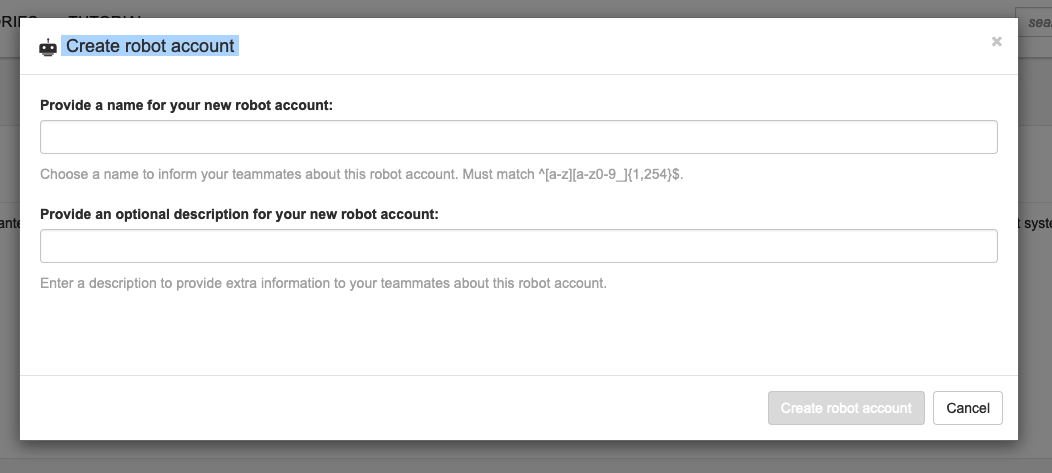
Click on Create robot account
| Provide a name for your new robot account: todo_demo_app_yourusername |
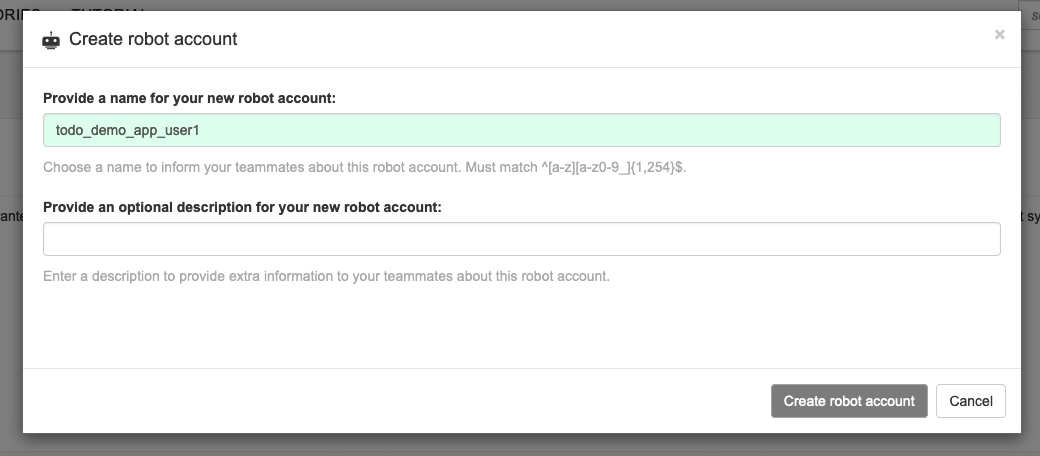
Add Permissions to the created account
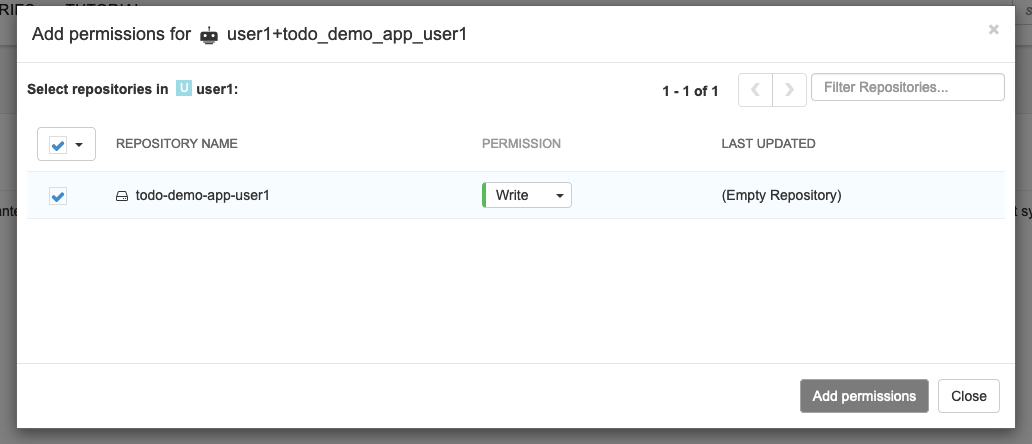
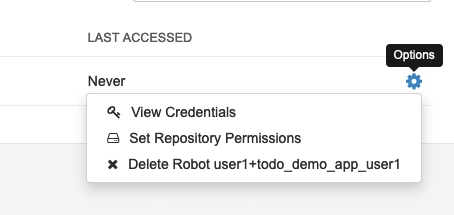
*Collect Credentials
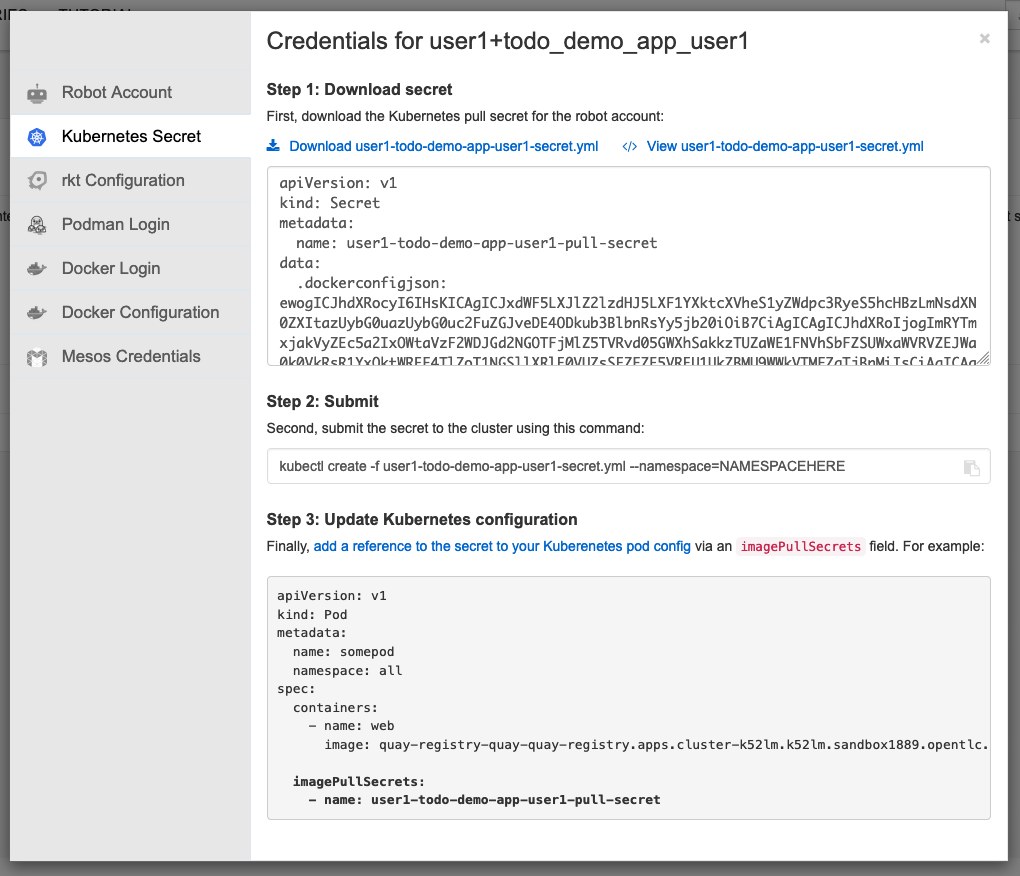
Configure OpenShift Secret
Copy secret into OpenShift with the name container-registry-secret-yourusername
| Click on Kubernetes Secret → View yourusername+todo_demo_app_yourusername.yaml |
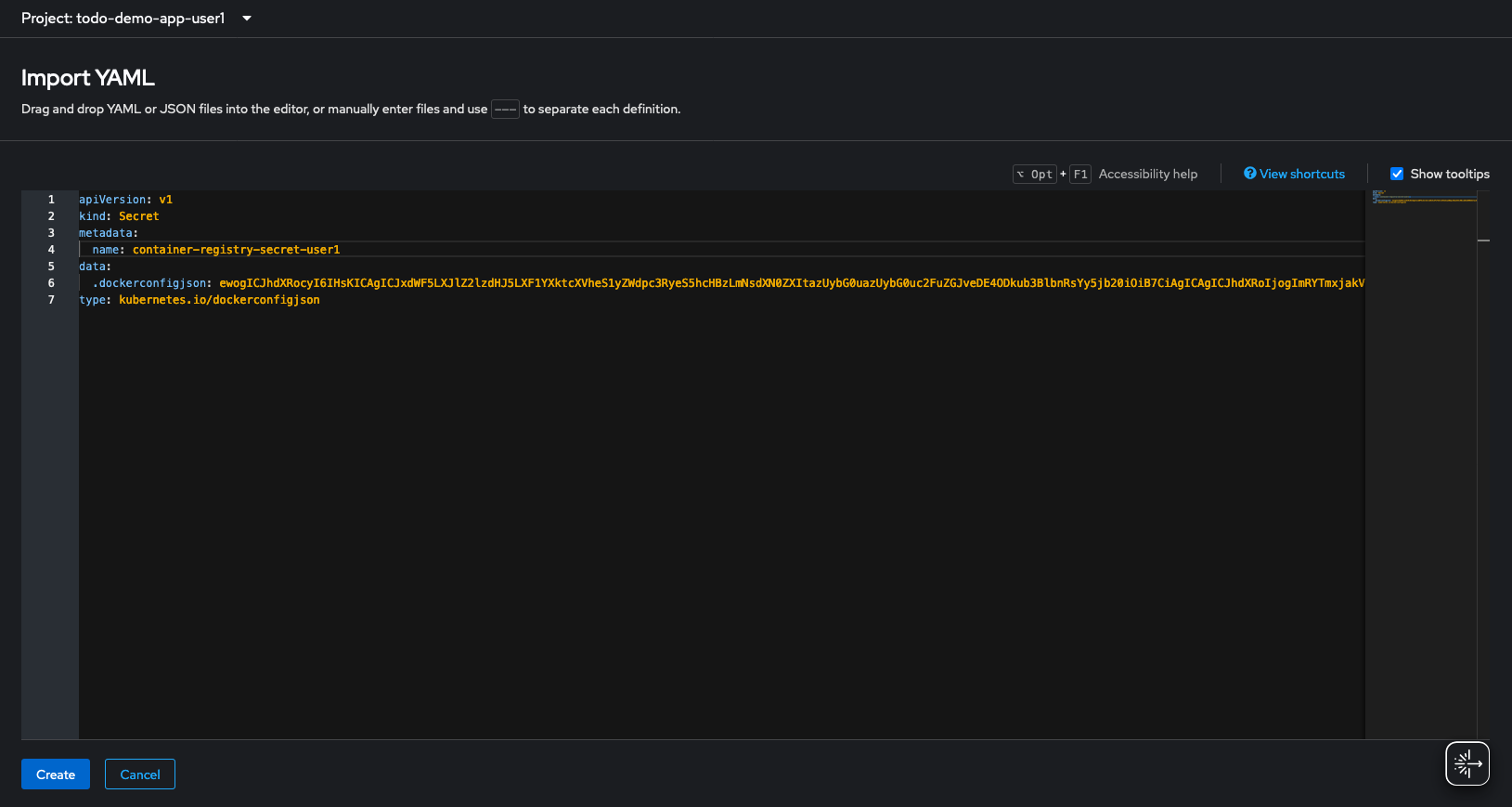
Copy secret into OpenShift with the name container-registry-secret-yourusername
| Use the + icon in the top right corner of the OpenShift console to quickly add YAML. Make sure you are in the todo-demo-app-yourusername! |
Module Summary
In this module, we explored the integration of Quay as a container registry with OpenShift Pipelines using Tekton. Key takeaways include:
-
Understanding the role of Quay in the CI/CD pipeline.
-
Configuing your repo with a Quay Pull secret for your Tekton Pipelines.
-
Pre-Configuring your enviornment to push images to Quay using Tekton Pipelines.